Preface
There are a lot of things to stay watchful for in our new age of technology. Whether it be a deepfake impersonation of a celebrity, or maybe even a family member. I wanted to take a moment to talk about something that happened today. You should probably be aware of this if you’re actively searching for jobs, and especially if you’re using LinkedIn.com
Scammers are using the LinkedIn job platform to harvest email addresses. They seem to be hijacking accounts from recruiters, though I can’t fully verify if these accounts are fraudulently created by them, hijacked, or a mixture of both.
They use these LinkedIn accounts to represent trustworthy businesses, and create job openings with LinkedIn’s Easy Apply feature. Some of them may be using a traditional job listing, but it is advantageous for them to take advantage of people that are looking to save time in their job search.
Detecting the scam:
You will give them your email that is tied to your LinkedIn account when you apply for these jobs, and from there, they will reach out beyond the LinkedIn platform. LinkedIn is essentially the gateway to information collection, and from there they can perform off-site operations to lead you into their scam.
They will use a legitimate organization, for example, Google, and use a malicious domain that impersonates the company.
Here is an example of how they would do this:
Legit Domain: Google.com
Malicious Domain: GoogleCareers.com
After freshly registering their domain name from a registrar, they will target a trustworthy figure in the company and create an email to make it look like it’s coming from them.
For example, Google’s CEO is Sundar Pichai, you could see something like:
Here’s an example of how this looks in the wild:

To establish credibility, they may link their website in the signature of the email as Google.com, so it appears like the legitimate Google when you do a brief check.
Easy Red Flags:
Here’s some major red flags that are a quick way to identify the scam:
- Freshly Registered Domain Name
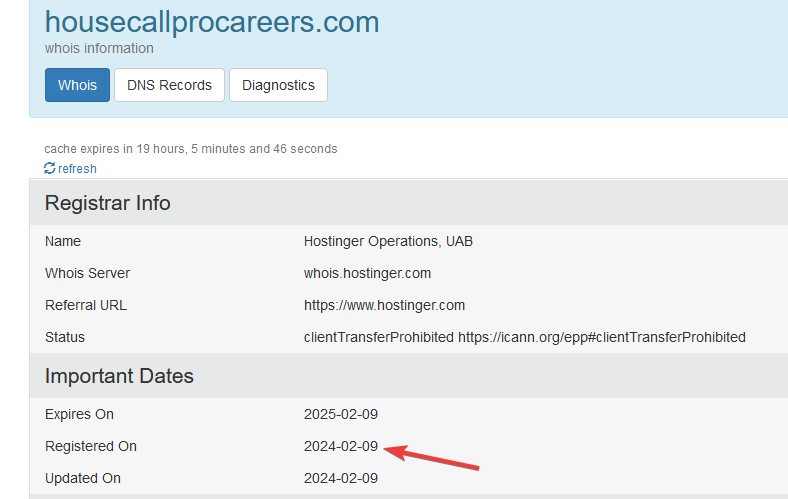
- You can use tools that allow you to view when the domain was created or registered. An established business would have an older domain, usually. I created a platform that curates a variety of tools, at ReportName.com, for stopping scams just like this. It provides an organized approach to reporting cybercrime and I’d encourage you to follow along using the ‘Research’ section to access the WHOIS search and easily perform a lookup. You can mark your progress with checkboxes to visually identify what tools you used.
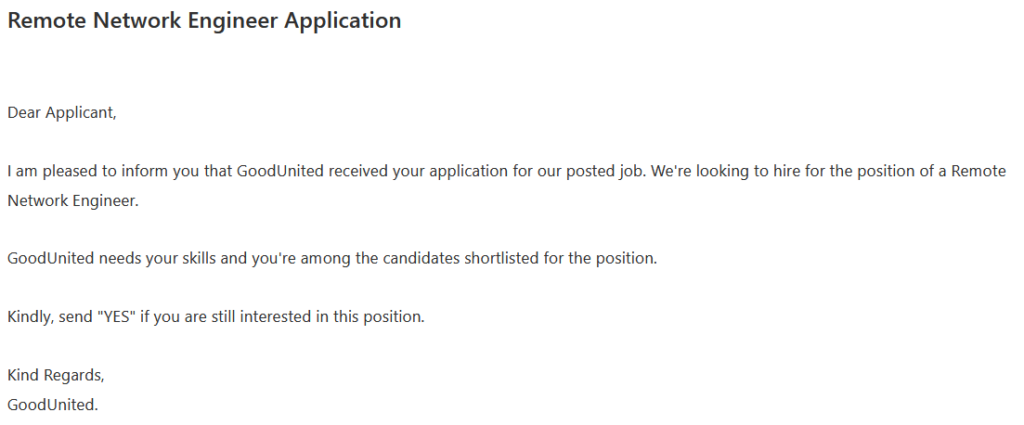
- Type “YES” to proceed (or something along those lines)
- This is probably a way for them to filter out people who are serious and attentive applicants, unfortunately a way for them to gauge who might be more likely to fall for their facade.
- Conflicting story, things not adding up, inaccuracies, too good to be true
- Multiple domain names can be a tip-off sometimes. In my case, I saw two different domain names, and it immediately reminded me of the first time I had encountered this scam. (Like, Google.com v. GoogleCareers.com), think to yourself, why would they be using both? Some companies do this so it’s not always an accurate metric, but it definitely causes me to research domain name history and age from there.
- Multiple domain names can be a tip-off sometimes. In my case, I saw two different domain names, and it immediately reminded me of the first time I had encountered this scam. (Like, Google.com v. GoogleCareers.com), think to yourself, why would they be using both? Some companies do this so it’s not always an accurate metric, but it definitely causes me to research domain name history and age from there.
- Anything about a check or financial excuse/time pressure.
- They will forge checks that are designed to bounce. Before they bounce, they will find some excuse to get you to pay them some amount of money through something like Zelle, Venmo, Bitcoin, PayPal, etc., – they get their fraudulent money, and you get their fake check.
- They will forge checks that are designed to bounce. Before they bounce, they will find some excuse to get you to pay them some amount of money through something like Zelle, Venmo, Bitcoin, PayPal, etc., – they get their fraudulent money, and you get their fake check.
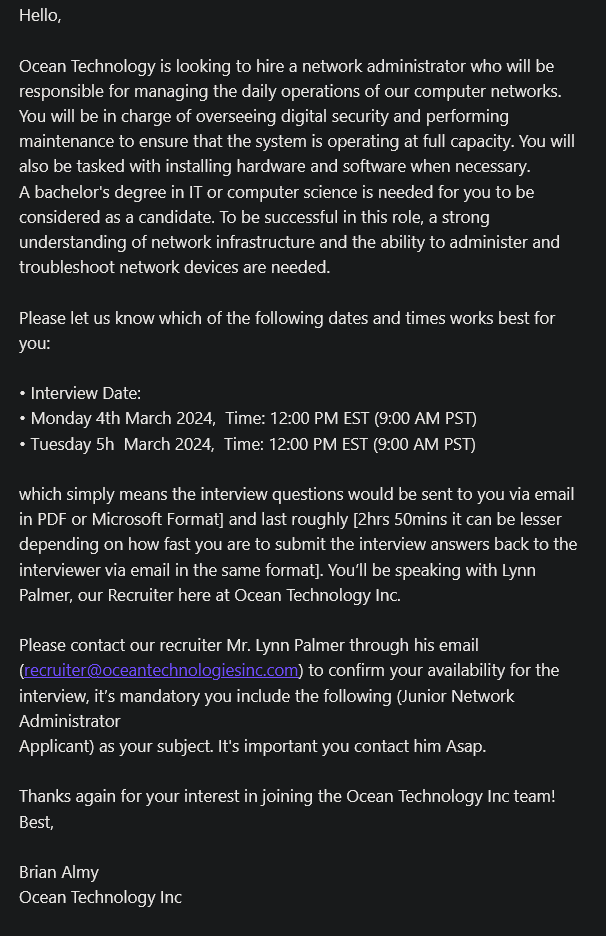
- Virtual interview process, especially if they try to do it via email.
- Astronomical salary in the PDF that they send you. Data suggests that this is to distract you as much as possible. Two data points confirmed (see below – Data Points) $124,000 – $135,000 annually for a remote technical support specialist. Use your judgment and look at the average market rate, then consider that this may be inflated for only one reason: to deceive. It may not always be this obvious, so stay cautious.
- Real people being impersonated:
- In many instances, I’ve been in direct cooperation with the real counterparts to ensure that they are made aware that there are people taking advantage of their brand identity.
- Sometimes they will use a real name, but the position of that person will not match up. Ex: In the scam that person is claimed to be the CEO, but the real person is a custodian, for example.
Data Points
Ex. 1
- Scammer Initial Email was May 1st, 2023.
- Impersonating domain was registered on May 1st, 2023.
- I reply “YES” to the scam email on May 1st, 2023.
- Scammer sends payload PDF interview questions. Contains realistic photo of company logo and about 20-30 questions related to network engineering.
- I reply to the questions.
- Scammer sends a congratulatory email around May 3rd 2023, and tells me the salary is about $60 an hour. Direct deposit for the pay.
Ex 2.
- Scammer Initial Email was at February 15th, 2024, 2:11 PM EST
- Impersonating domain was registered on February 9th, 2024.
- I reply “YES” to the scam email on February 15th, 2024
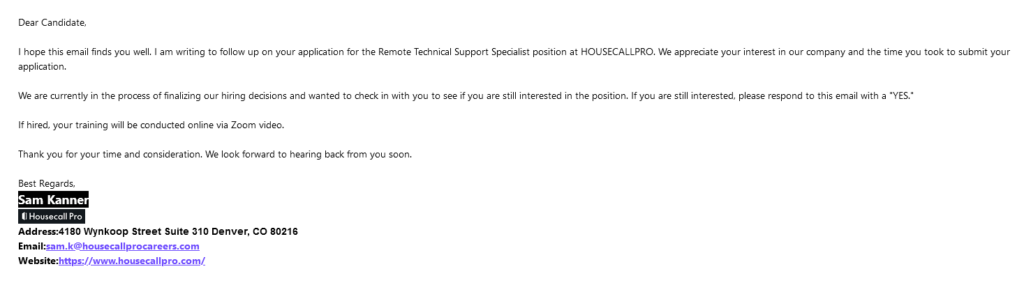
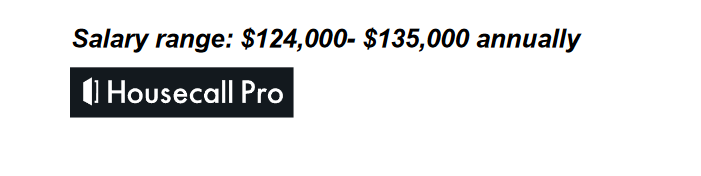
- Scammer sends payload, “Housecallpro Screening Questions.pdf” for data collection. PDF contains realistic interview questions and contains company logo image at the top. Salary range is $124,000-,$135,000 annually for a TECHNICAL SUPPORT SPECIALIST REMOTE ROLE. Astronomical salary.
Additional Encounters:
Red flag – Virtual interview
Red flag – Typo
Red flag – Recently registered domain name
Red flag – Requesting to email via a different domain than original sender domain (this is sort of like someone trying to detach from the origin. Think of this like if you had crypto from one wallet, sent to another wallet, to make it harder to trace. Sort of like that, but for email)
Red flag – impersonation of credible business / individual
Stay safe!
I have a project I’m working on that requires malicious email data. You can contribute to my database by forwarding anything unusual or suspicious to [email protected]
In all the examples above, the real companies are already aware, but I strongly encourage you to contribute to a safer internet by reporting these domains when you find yourself able to. Use the Report Domain Name list at http://ReportName.com for a curated list of all the report-abuse forms. You can also submit links you’d like to see on ReportName and I’ll happily add them.
Lessons Learned
I’m very tired of these scams that I encounter in my daily job search. I’m sure you are too. I try to tie in every blog post with a lesson, and today’s lesson is that despite our frustrations, sometimes it can fuel us to do things in the world we would have never thought we could do before. I encourage you to use your frustration as an energy source for a world-changing solution. Always remember to take a step back and think about the situation. Do not be afraid to ask questions, and do not be ashamed. You are not stupid if you fall for these things. They are designed to hack our brains.
BOOM!
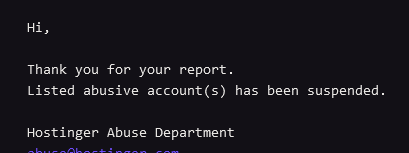
The scam site has been taken down. Your reporting efforts are worth your time.
Resources:
An organized approach to reporting cybercrime, ReportName.com
[email protected] to contribute to the weird email database 🙂
Old Post Referencing this kind of scam:
Thank you for reading. Ways to support me:
Free and Open Source Windows Application, Task Runway:
An organized approach to reporting cybercrime, ReportName.com:
Donate:
https://www.davidinfosec.com/donate
